User IP Address Leakage via Unproxied External Resources
Introduction
Recently I was hunting on a target when I discovered a privacy issue that could allow malicious actors to deanonymize users.
Privacy leaks are often overlooked in bug bounties, but when a vulnerability allows an attacker to correlate a user's identity with their real-world physical location (via IP address), the impact becomes significant. Here is how I found it.
The Discovery
While testing the profile settings, I noticed the "Profile Picture" feature allowed users to upload images via URL. I immediately wondered: Does the server download this image and host it? Or does it force every visitor's browser to fetch it directly?
I realized that the application was loading external resources directly from third-party servers without proxying the request through their backend. This meant that if I could control the image URL, I could see the IP address of anyone who viewed my profile.
The Exploitation
Step 1: The Setup
To verify this, I needed a server that I controlled to capture the incoming requests. I used an OAST (Out-of-Band Application Security Testing) service to generate a payload.
I set my profile picture URL to my controlled domain:
https://[attacker-domain].oast.fun/.png
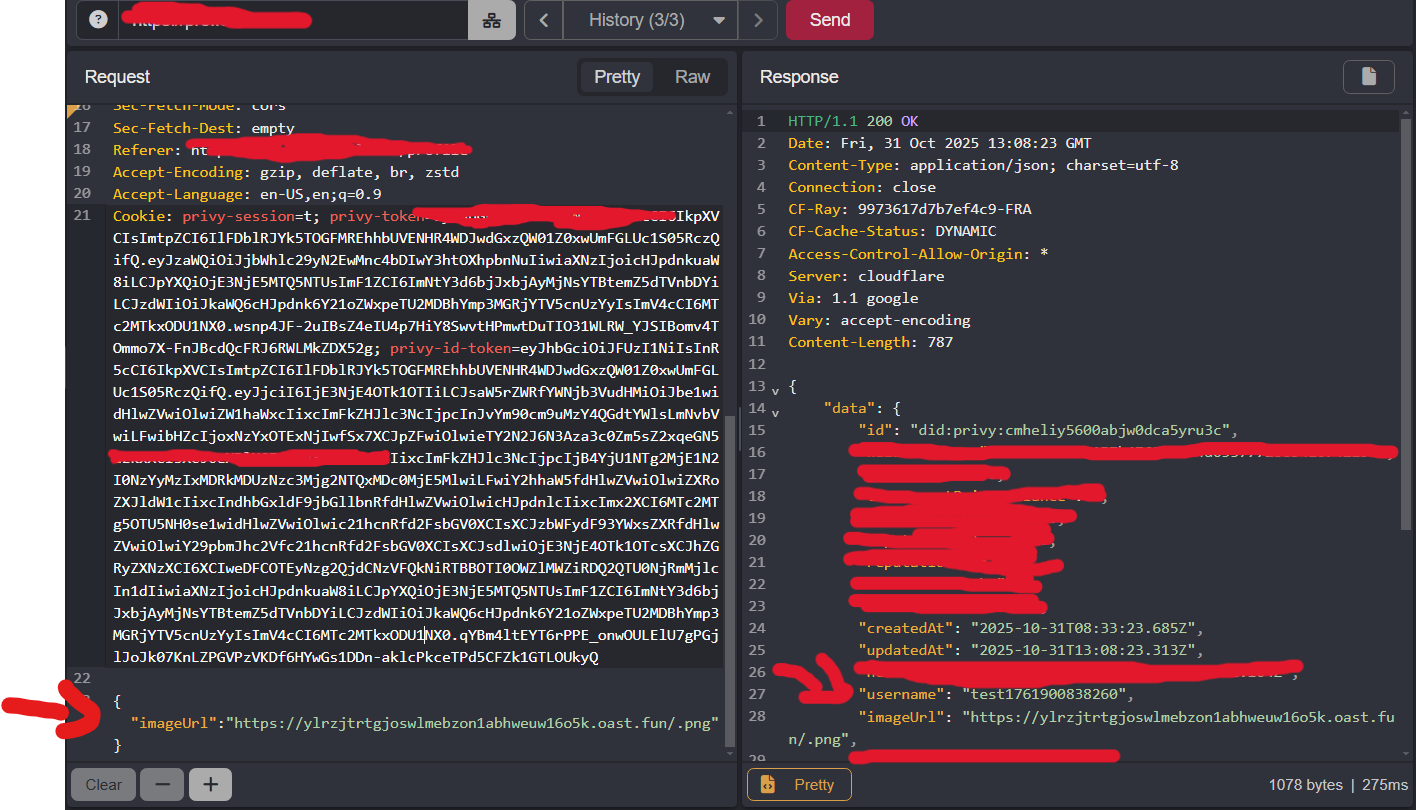 Figure 1: Injecting the external payload into the profile picture input.
Figure 1: Injecting the external payload into the profile picture input.
Step 2: Triggering the Leak
Once the profile picture was saved, the trap was set. When any user, or even an admin, views the profile, their browser tries to render the image. To do so, it sends a GET request to my server.
.png) Figure 2: The browser automatically making the request to the external source.
Figure 2: The browser automatically making the request to the external source.
Step 3: Confirmation
Checking my server logs, I received immediate confirmation. The logs revealed the Real IP address, the User-Agent (browser and OS info), and the Referer header of the victim.
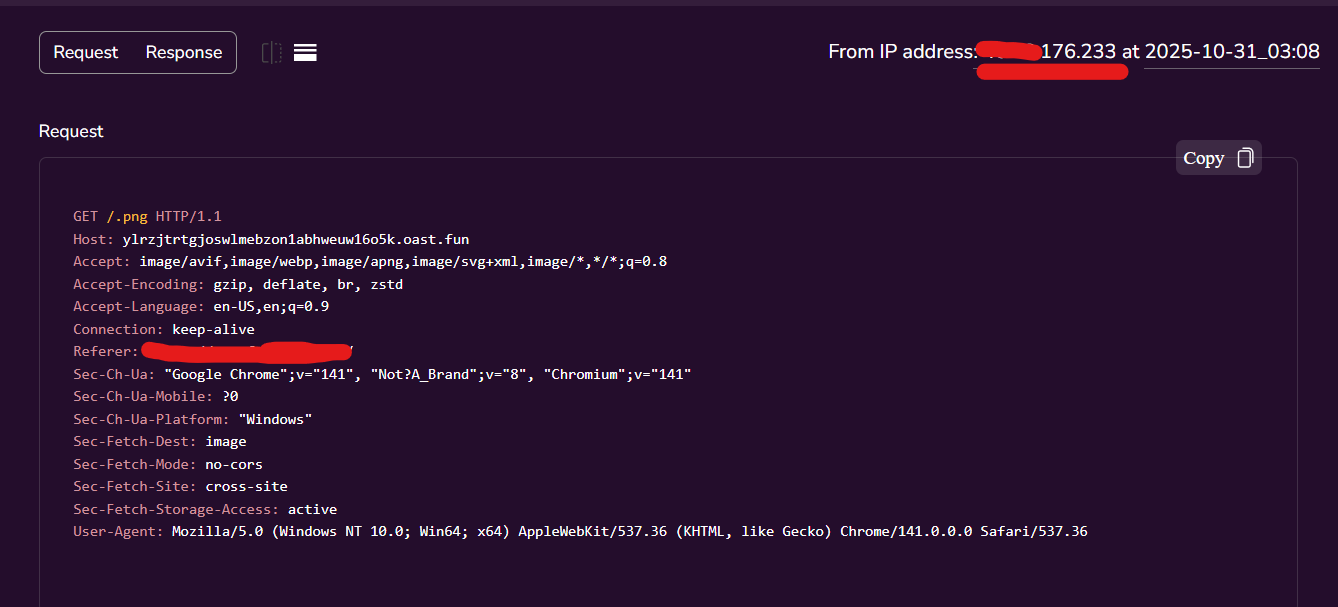 Figure 3: My server logs capturing the victim's IP address and User-Agent.
Figure 3: My server logs capturing the victim's IP address and User-Agent.
Why This Matters
This vulnerability allows an attacker to de-anonymize users. On a platform like this, where users might want to remain pseudonymous, linking an account to a physical home IP address is a privacy violation. The impact is amplified if a malicious actor places themselves on the Leaderboard, potentially harvesting data from hundreds of users passively.
The Fix
I recommended to the team that they implement an image proxy to serve external profile pictures through their own infrastructure. This prevents direct requests from user browsers to external domains. This approach is standard practice on platforms like Discord, Reddit, and Slack.
Timeline & Payout
The team was quick to respond and validated the finding. They assessed it as Medium Severity and rewarded a bounty of $1,675.
 Figure 4: Bounty confirmation.
Figure 4: Bounty confirmation.
Written by s8n.